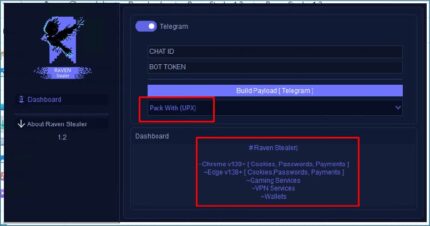
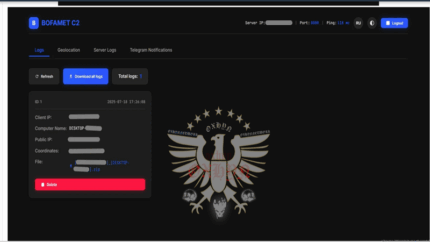
A sophisticated new infostealer and botnet named “Cyber Stealer” was discovered by eSentire’s Threat Response Unit (TRU) in May 2025. This multi-purpose malware combines advanced information stealing capabilities with botnet functionality, creating a versatile attack platform. Cyber Stealer operates on a tiered subscription model with three distinct packages:
———————————————————————————————————————————————————————————–
The malware’s information stealing components target a comprehensive range of applications and services, including:
-
Web browsers and their stored credentials
-
Cryptocurrency wallets
-
Communication platforms
-
Gaming applications
-
Development tools
-
Email services
-
Cloud storage platforms
-
Password managers
-
VPN clients
———————————————————————————————————————————————————————————–
CyberStealer extracts stored passwords, cookies, and autofill data from browsers, captures keystrokes, collects cryptocurrency wallet files, and records system details. The harvested information is then transmitted to a command-and-control server controlled by attackers.
Beyond data theft, Cyber Stealer’s botnet capabilities enable threat actors to:
-
Download/execute additional malware
-
Conduct keylogging attacks to harvest victim keystrokes
-
Launch DDoS attacks
-
Mine cryptocurrency
-
Establish reverse proxies
-
Access remote shells
-
Replace victims’ clipboard with threat actor controlled crypto-currency wallet addresses
———————————————————————————————————————————————————————————–
Key Features
A comprehensive list of key features marketed by the threat actor are included below.
Browsers |
Google Chrome, Mozilla Firefox, Microsoft Edge, Brave, Opera / Opera GX, Vivaldi, Yandex, Comodo Dragon, Orbitum, Amigo, Torch, Kometa |
Browser Data |
Passwords, Cookies, History, Credit Cards, Autofill, Bookmarks, Extensions, Session Data, IndexedDB, Cache, Login Data, Site Preferences |
Crypto-wallets (desktop) |
Atomic Wallet, Exodus, Jaxx Liberty, Electrum, Bitcoin Core, Ethereum Wallet, MetaMask Desktop, Coinomi, Ledger Live, Trezor Suite, Daedalus (Cardano), Yoroi, Monero GUI, Wasabi Wallet, Green Wallet, Electrum-LTC, Dogecoin Core, Trust Wallet Desktop, Phantom Desktop |
Crypto-wallets (browser) |
MetaMask, Binance Chain Wallet, Coinbase Wallet, Phantom (Solana), Keplr, Terra Station, Sollet, Math Wallet, Coin98, SafePal, TokenPocket, Rabby, OKX Wallet, BitKeep, WalletConnect, Slope, Petra, Pontem, Martian, Temple (Tezos), Enkrypt, GameStop, Zerion, Rainbow, Frame, Taho, Core, XDEFI |
Crypto Exchanges |
Binance, Coinbase, Kraken, KuCoin, Bitfinex, Huobi, OKX, Bybit, Gate.io, Gemini, BitMart, Crypto.com, Bittrex, Poloniex, WhiteBIT, MEXC, Bitstamp, Phemex, Bitpanda, LocalBitcoins, Paxful, Bisq |
DeFi Platforms |
PancakeSwap, Uniswap, SushiSwap, Curve, 1inch, TraderJoe, GMX, DYDX, Perpetual Protocol, Synthetix, Aave, Compound, MakerDAO, Lido, Convex |
Messaging/Communication Apps |
Telegram, Discord, Element, Signal, WhatsApp, Viber, Skype, Microsoft Teams, Slack, Google Hangouts, Google Meet, Google Chat, Facebook, Messenger Yahoo, Messenger, QQ, Snapchat, TikTok, Instagram, Facebook, Twitter, Wire, Threema, VK, KakaoTalk, Zoom, WeChat, Line, ICQ, Matrix clients |
Gaming Clients |
Steam, Epic, Games, Riot, Games, Battle.net, Ubisoft Connect, EA Desktop, GOG Galaxy, Xbox, Rockstar, Roblox, Minecraft Launcher |
Developer Tools |
VS Code, IntelliJ, PyCharm, Eclipse, Android Studio, NetBeans, Xcode |
FTP/RMM Tools |
FileZilla, WinSCP, PuTTY, TeamViewer, AnyDesk, RDP |
Cloud Tools |
Docker, Kubernetes, CLI, AWS CLI, GCP SDK, Heroku CLI |
Cloud Storage |
Google Drive, Dropbox, OneDrive, MEGA, iCloud, Box, pCloud, Proton Drive, Tresorit, Sync.com |
Email Clients |
Outlook, Thunderbird, EM Client, Windows Mail, Apple Mail, Opera Mail, Zimbra, PostBox, The Bat! |
Password Managers |
Bitwarden, KeePass, 1Password, LastPass, Dashlane, NordPass, Keeper, RoboForm, Sticky Password, Buttercup, Enpass |
VPN Clients |
NordVPN, OpenVPN, ProtonVPN, ExpressVPN, CyberGhost, Private Internet Access, Surfshark, VyprVPN, IPVanish, TunnelBear, Mullvad, Windscribe, HideMe, PureVPN, HotspotShield, ZenMate, AvastVPN, AVG VPN, FastestVPN, AtlasVPN, BetterNet, Urban, X-VPN, Speedify, TouchVPN, Kaspersky VPN, Bitdefender VPN, Norton VPN, McAfee SafeConnect, F-Secure VPN |
System/Security Info |
Antivirus data, Windows credentials, Digital certificates, Saved Wi-Fi keys, SSH / GPG keys, Scheduled tasks, Registry data, Group policy settings, Logs and system info, Installed applications |
Monitoring/Logging |
Keylogger, Real-time screenshot capture, Tasks (download and execute, update), Searchable logs, filters, and botkiller |
Bot Management/Visualization |
Bot map visualization, Status counters, Live connection display, Adding note and to favorites |
Task Management/Scheduler |
Download and execute, Update bot with new payload, Execution tracking, Task history, Backup of all logs and task data |
Telegram Notification System |
Instant alerts for new logs, bot activity, receiving logs zip files via Telegram |
DNS Spoofing Module (Poisoning) |
DNS poisoning functionality, enabling redirection of targeted domain names to custom IP addresses. |
Clipper |
Advanced crypto clipper module that monitors the system clipboard and replaces copied cryptocurrency addresses with predefined addresses. |
DDoS |
Attack methods supported: TCP, UDP, HTTP, SYN, ICMP, Slowloris, DNS Amplification |
Silent Mining |
Fully undetectable background mining, Auto-detects system hardware to know which coin to mine for highest profitability |
Reverse Proxy |
Use the bot’s IP as your own to bypass 2FA or to make your own proxy list from bots. If you have 1,000 bots, you will have 1,000 online proxies that you can sell |
Remote Shell |
Remote cmd and PowerShell execution on the bots |